June 2023 Patch Tuesday: 78 Vulnerabilities with 6 Rated Critical and 38 Remote Code Execution
Microsoft has released 78 security patches for its June 2023 Patch Tuesday rollout. Of the vulnerabilities patched today, 6 are classified as Critical and 38 are remote code execution (RCE) flaws. June 2023 Risk Analysis This month’s leading risk type is remote code execution (41%), followed by elevation of privilege at nearly 22% and a […]

Microsoft has released 78 security patches for its June 2023 Patch Tuesday rollout. Of the vulnerabilities patched today, 6 are classified as Critical and 38 are remote code execution (RCE) flaws.
June 2023 Risk Analysis
This month’s leading risk type is remote code execution (41%), followed by elevation of privilege at nearly 22% and a tie for denial of service and spoofing at 13% each.
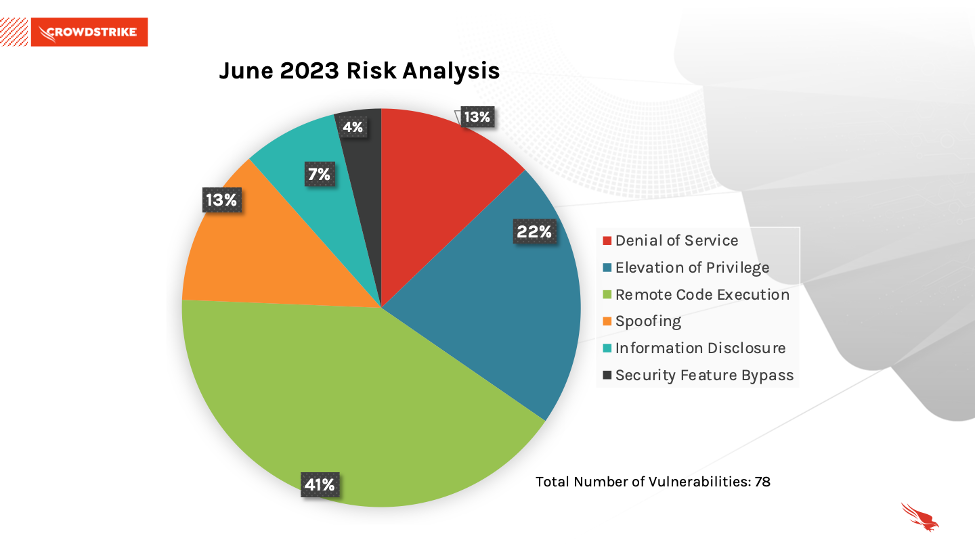
Figure 1. Breakdown of June 2023 Patch Tuesday attack types
The Microsoft Windows product family received the most patches this month with 37, followed by Developer Tools with 25 and Extended Security Update (ESU) with 18.
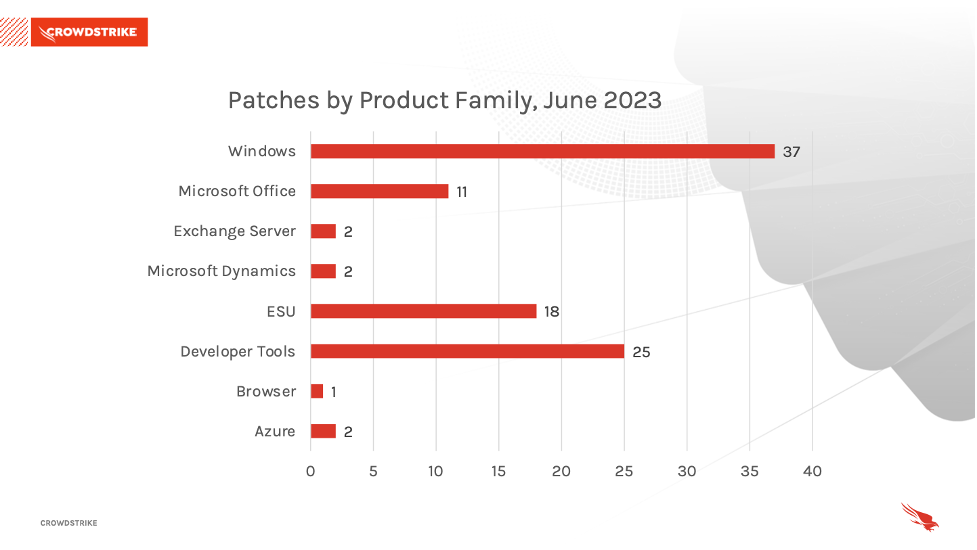
Figure 2. Breakdown of product families affected by June 2023 Patch Tuesday
Critical Vulnerability in Microsoft SharePoint Server
Microsoft Office is getting a patch for Critical vulnerability CVE-2023-29357, which has a CVSS of 9.8. SharePoint is a powerful collaboration platform that lets organizations share and manage content, knowledge and applications. The Microsoft Security Response Center (MSRC) says an attacker that gains access to spoofed JSON Web Tokens (JWT) can leverage them to execute a network-based attack that bypasses authentication and allows them to potentially access administrator privileges.
Microsoft states, “Customers who have enabled the AMSI integration feature and use Microsoft Defender across their SharePoint Server farm(s) are protected from this vulnerability. For more information, see Configure AMSI integration with SharePoint Server.”
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2023-29357 | Microsoft SharePoint Server Elevation of Privilege Vulnerability |
Figure 3. Critical vulnerability in Microsoft SharePoint Server
Critical Vulnerabilities Affect Windows Pragmatic General Multicast
CVE-2023-29363, CVE-2023-32014 and CVE-2023-32015 are three Critical distinct vulnerabilities with a CVSS of 9.8. Microsoft Windows Pragmatic General Multicast (PGM) has been updated in the last two monthly patch releases. In this particular case, the vulnerabilities allow a remote, unauthenticated attacker to execute code on an affected system when the Windows Message Queuing service is running in a PGM server environment. As Microsoft states in the description for each CVE: “The Windows message queuing service, which is a Windows component, needs to be enabled for a system to be exploitable by this vulnerability. This feature can be added via the Control Panel. You can check to see if there is a service running named Message Queuing and TCP port 1801 is listening on the machine.”
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2023-29363 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-32014 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-32015 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
Figure 4. Critical vulnerabilities in MS Windows Pragmatic General Multicast (PGM)
Critical Vulnerability Affects Windows Hyper-V
CVE-2023-32013 is a Critical vulnerability affecting Windows Hyper-V with a CVSS of 6.5. Hyper-V is Microsoft’s virtualization platform that enables administrators to simultaneously run multiple operating systems on the same physical server. According to Microsoft, “Successful exploitation of this vulnerability requires an attacker to prepare the target environment to improve exploit reliability.” It is likely this vulnerability is rated “Critical” despite the otherwise lower CVSS score because of the importance of Hyper-V on virtualization infrastructures and the ease of access through the network as an attack vector.
| Rank | CVSS Score | CVE | Description |
| Critical | 6.5 | CVE-2023-32013 | Windows Hyper-V Denial of Service Vulnerability |
Figure 5. Critical vulnerability in MS Windows Hyper-V
Critical Vulnerability Affects .NET, .NET Framework and Visual Studio
CVE-2023-24897 is a Critical vulnerability affecting Windows .NET, .NET Framework and Visual Studio and has a CVSS of 7.8. .NET and Visual Studio are used to create a variety of business and scientific systems. This particular vulnerability has “remote” in the title but according to Microsoft, “The word Remote in the title refers to the location of the attacker. This type of exploit is sometimes referred to as Arbitrary Code Execution (ACE). The attack itself is carried out locally.”
| Rank | CVSS Score | CVE | Description |
| Critical | 7.8 | CVE-2023-24897 | .NET, .NET Framework and Visual Studio Remote Code Execution Vulnerability |
Figure 6. Critical vulnerability in .NET, .NET Framework and Visual Studio
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j, not every highly exploitable vulnerability can be easily patched. As is the case for the ProxyNotShell vulnerabilities, it’s critically important to develop a response plan for how to defend your environments when no patching protocol exists.
Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization’s methods for cybersecurity and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events every day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.
Learn More
Learn more about how CrowdStrike Falcon® Spotlight vulnerability management can help you quickly and easily discover and prioritize vulnerabilities here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on which products are in Microsoft’s Extended Security Updates program, refer to the vendor guidance here.
- Download the CrowdStrike 2023 Global Threat Report to learn how the threat landscape has shifted in the past year and understand the adversary behavior driving these shifts.
- See how Falcon Spotlight can help you discover and manage vulnerabilities and prioritize patches in your environments.
- Learn how CrowdStrike’s external attack surface module, Falcon Surface, can discover unknown, exposed and vulnerable internet-facing assets enabling security teams to stop adversaries in their tracks.
- Learn how Falcon identity protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent.






































