Patchstack reports on the fake CVE Phishing Campaign used to force WordPress users to install malware
For the past couple of days, the Patchstack team has been monitoring a mass-scale phishing campaign with multiple variants of phishing emails going around that are notifying users about a supposed security vulnerability in their WordPress website. They claim it’s a “Remote Code Execution (RCE)” vulnerability and you are asked to immediately use this patch created by the WordPress Team to patch the vulnerability with...
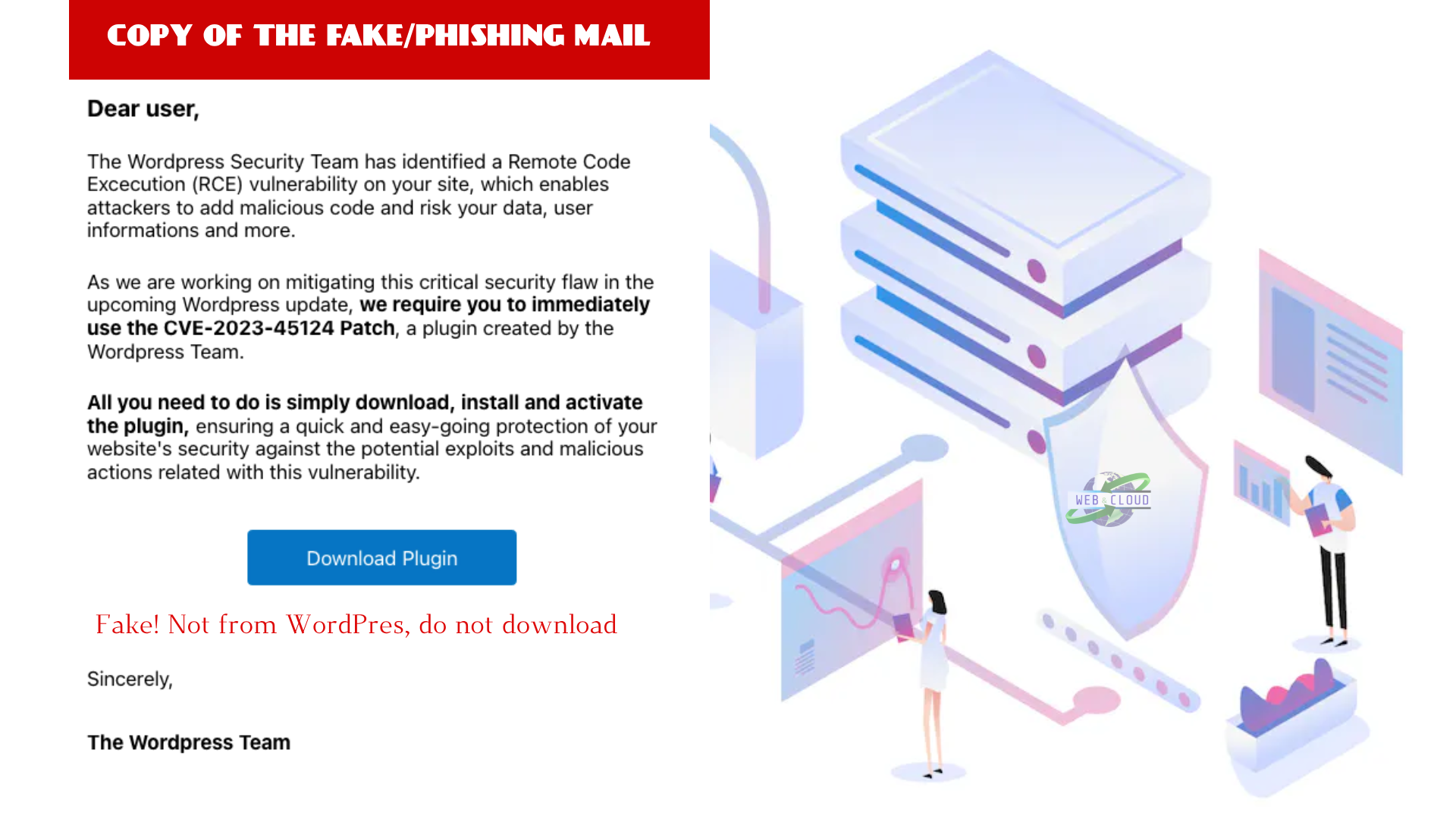
Overview of the phishing page
Once you click on the download plugin button in the email, you will be directed to a site that has cloned the WordPress.org site as seen below. This includes domain names like wordpress[.]secureplatform[.]org and en-gb-wordpress[.]org.
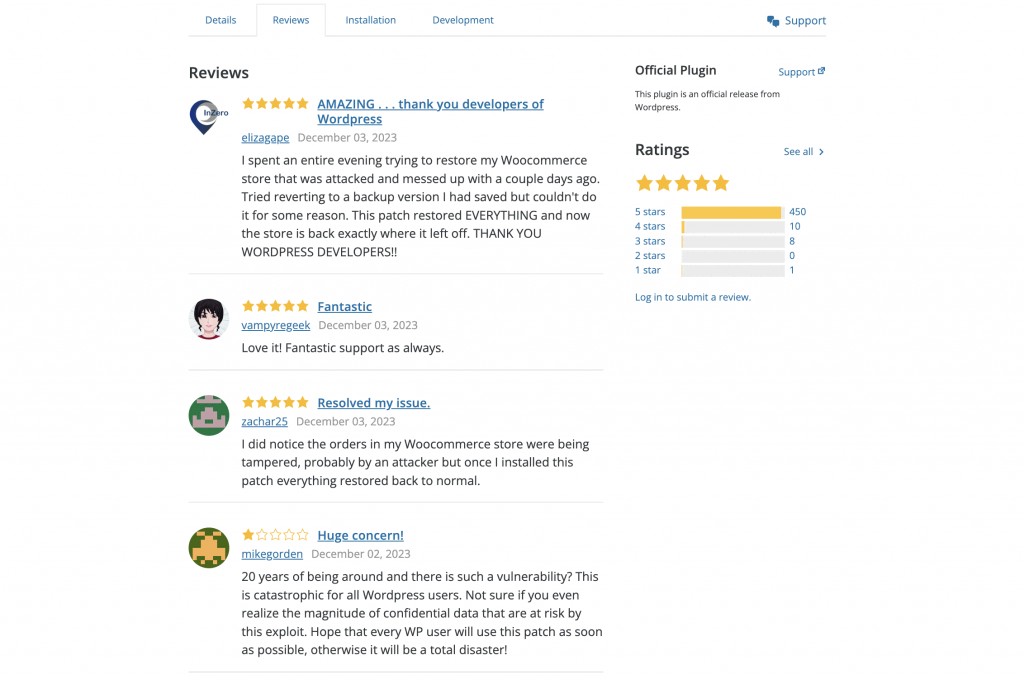
The attackers have even written fake reviews on the same page, which leaves an impression as if real WordPress users are being thankful to this patch being released.
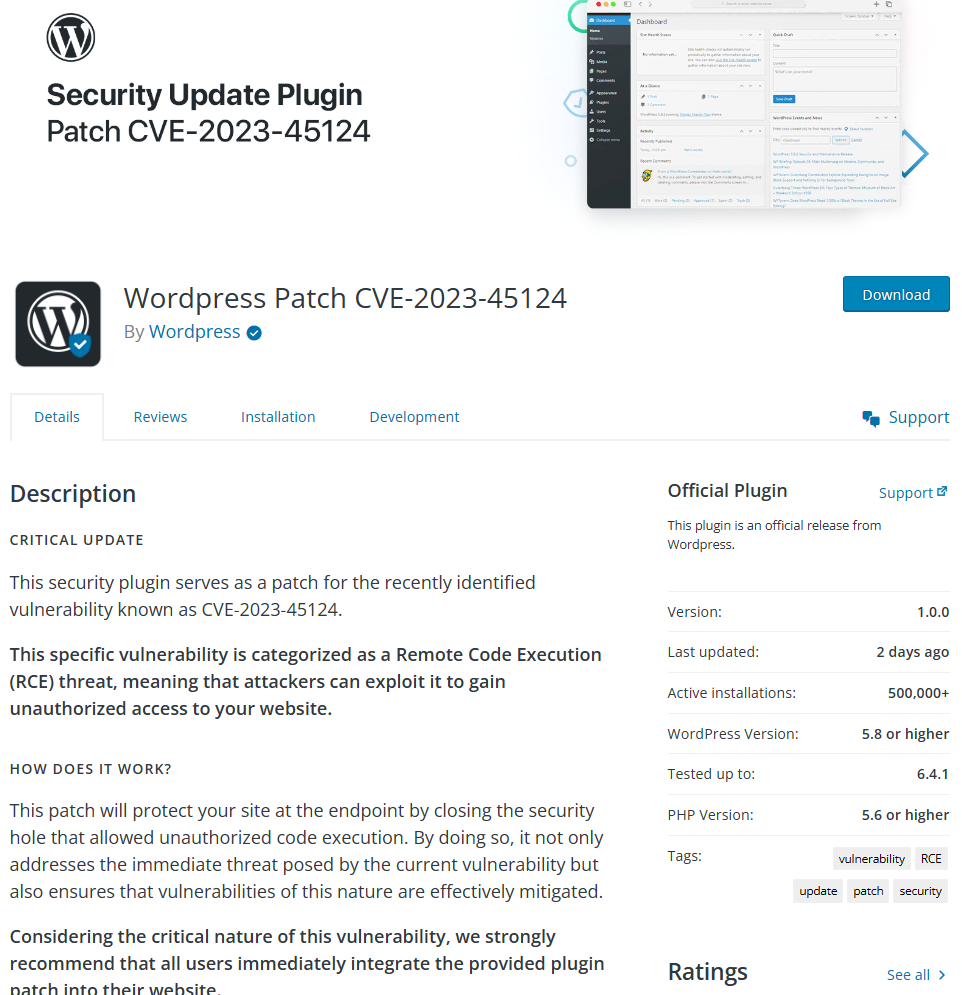
Interestingly, the attackers have also targeted some known people from the WordPress ecosystem by presenting them as authors of this “patching” plugin. Most of the people listed are the core contributors and employees of Automattic. Some listed people are also behind known WordPress agencies such as 10up and MindSize.
Technical analysis of the CVE phishing campaign malware
Once you download the plugin, you will be served a download with a filename of the CVE phishing campaign such as cve-2023-45124.zip. This varies by domain name they have used for this phishing campaign, we have also seen other filenames for the zip file.
Once you install and activate the plugin, it will show “CVE-2023-45124 has been patched successfully” and “We encourage you to share this patch with people you think might be affected by this vulnerability.” to get as many infections as possible.
What actually happens is the following:
- A random password will be created for a username (wpsecuritypatch) that will be created with administrator privileges.
- A HTTP GET request is sent to their server, in one case wpgate[.]zip/wpapi with a siteurl query parameter that contains base64 encoded data of the URL of the site they infected as well as the password of the administrator account they created.
- A HTTP GET request is sent to wpgate[.]zip/runscan which returns base64 encoded data which they base64 decode in the malicious plugin and then attempt to insert into a wp-autoload.php file which will be copied to the root folder of the WordPress site.
- The plugin will then hide itself from the plugin list as well as hiding the administrator account that it created.
On the screenshot below you can find a portion of the code of this malicious plugin. Ironically, the comments written by the malicious user directly tell you what the malicious code under it is doing.

After this, the wp-autoload.php backdoor that has been created will likely be utilized at a future point in time for further exploitation, most likely for any of the following:
- Injecting advertisements into the site.
- Redirecting users to a malicious site.
- Utilizing the backdoor for DDoS attacks along with all the other infected sites.
- Stealing billing information.
- Blackmailing, for example by making a copy of the database and then holding it hostage for a cryptocurrency payment.
This wp-autoload.php backdoor is essentially identical to the P.A.S. backdoor, an example can be found on the GitHub repository here: https://github.com/cr1f/P.A.S.-Fork/blob/main/pas_fork.php
Indicators of compromise:
- A user with the username wpsecuritypatch has been created.
- A file called wp-autoload.php is present in the root folder of your WordPress site.
- A folder called wpress-security-wordpress or cve-2023-45124 exist in the /wp-content/plugins/ folder.
- Outgoing requests sent to wpgate[.]zip
As always, it is very likely for any of the above variables to change to something else. Tomorrow they could very well have the username set to something else or set up another malicious domain name.
Patchstack will monitor the logs of our customers and has also attached a new rule to the “Advanced Hardening” module that will attempt to block any installation attempts by our customers to install this malicious plugin.
If you have any questions about the CVE phishing campaign or need any help contact the Patchstack team.